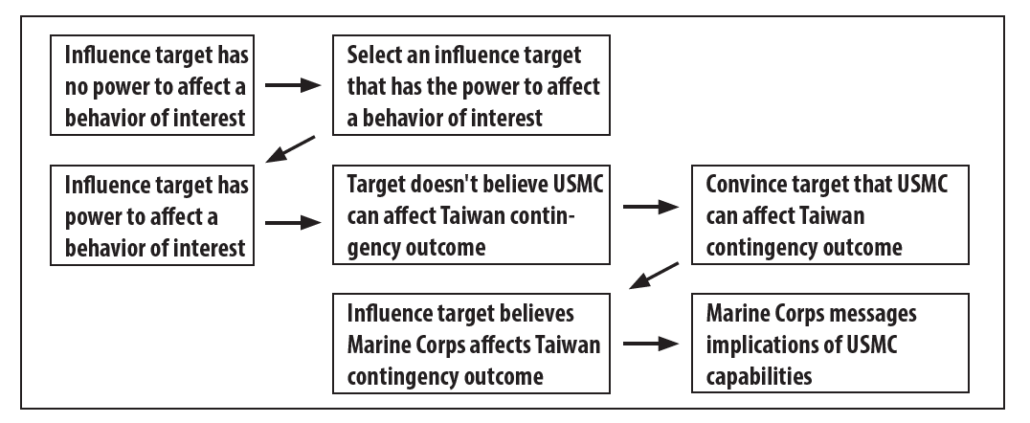
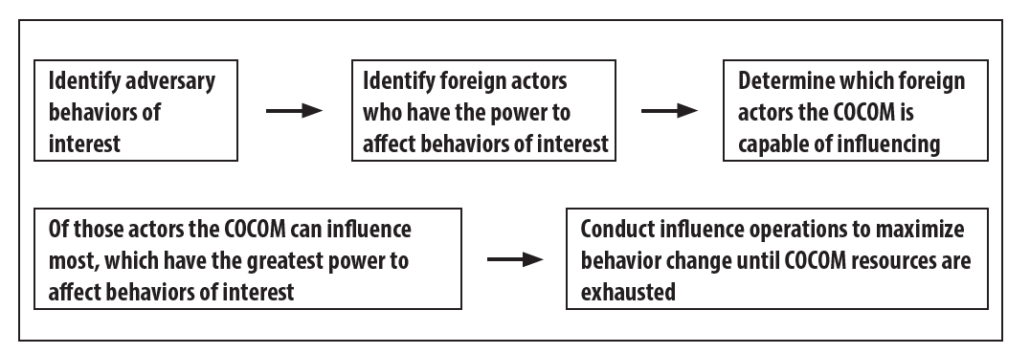
Understanding the pacing threat
The dawn of a new year is a most appropriate and auspicious time to take stock of oneself, one’s goals, and one’s path forward for the next twelve months—a veritable fulcrum of reflection. And what better subject matter to consider in rectifying one’s ways than the governing ideology (to loosely use the term) of Chairman Xi Jinping, the paramount leader of the Chinese Communist Party (CCP), its military wing, the People’s Liberation Army (PLA), and the People’s Republic of China (PRC) over which he governs?
Often framed as the “pacing threat” for the Marine Corps and broader Joint Force, the CCP-PRC Party-State under Chairman Xi has recommitted itself to an ideological nationalism formally termed “Xi Jinping Thought on Socialism with Chinese Characteristics for a New Era” (习近平新时代中国特色社会主义思想), more commonly known as “Xi Jinping Thought.”1 First announced by General Secretary Xi Jinping at the 19th National Congress of the CCP in October 2017, “Xi Jinping Thought”2 now resides in the CCP’s constitution3 and serves as a guiding4 doctrine5 for all levels of the Party-State6 to “rejuvenate the nation” and achieve the “China Dream.”7
A key enabler for China’s “national rejuvenation” is victory in the information domain at home and abroad. Beijing’s recent efforts to manipulate domestic and foreign perceptions through digitally enabled hearts-and-minds campaigns are well-documented. Effective prosecution of the same will allow the CCP and PLA to shape battlefields to their advantage without a shot being fired. As those efforts begin on the PRC’s home front, it behooves practitioners of information operations within the Marine Corps and broader defense enterprise to develop familiarity with the Fourteen Commitments, or guiding principles, that form the heart of “Xi Jinping Thought.”
1. “Ensure the Communist Party leads over all forms of work in China.” Since Chairman Xi’s accession in 2012, the CCP has reasserted its control over state,8 academic,9 and private-sector institutions.10 This comprehensive approach to governance integrates Party leadership at every level of society, ensuring that the Party’s directives and ideology influence all aspects of governance and daily operations.11 By embedding its presence deeply within these sectors, the CCP aims to maintain ideological consistency and reinforce its authoritative role, effectively centralizing power and establishing a uniform policy execution across the nation.
2. “Commit to a people-centered approach.” The Party-state’s reassertion of influence in all facets of Chinese life is balanced with a focus on the social needs of the people. Xi Jinping emphasizes “common prosperity”12 to address13 the growing wealth gap14 in China, reflecting his intent to ensure equitable economic development. This approach seeks to temper economic policies with social welfare initiatives, striving to uplift disadvantaged communities and foster a more inclusive society. By prioritizing the well-being of the people, the Party aims to strengthen social stability and reinforce its legitimacy among the populace.
3. “Comprehensively deepen reforms.” Xi Jinping’s assertion that “only socialism can save China, and only reform and opening-up can develop China” underscores his commitment to evolving socialism and Marxism. Since 2012, Xi has championed reforms15 to fortify Party-State control16 over China’s economy,17 society,18 and military.19 These reforms aim to enhance governance, boost economic efficiency, and ensure social stability. By integrating socialist principles with pragmatic reforms, Xi seeks to modernize China while maintaining the ideological foundation of the Communist Party, thereby reinforcing its authority and guiding the nation’s development trajectory.
4. “Adhere to new development ideas.” Xi Jinping emphasizes “scientific development” as the cornerstone for addressing China’s comprehensive challenges. This approach—characterized by coordinated, innovative, open, and green development—is designed to foster sustainable growth. Chairman Xi frequently frames20 CCP initiatives as “scientific”21 and “pragmatic”22 solutions, aiming to modernize the economy, enhance technological innovation, and promote environmental sustainability. By advocating for these development ideas, Xi seeks to ensure that China’s progress is both resilient and inclusive, addressing immediate needs while safeguarding future generations.
5. “Follow socialism with Chinese characteristics,” wherein “people are the masters of the country.” Chairman Xi frequently emphasizes23 that the development of the state24 should not take precedence over the people’s livelihood.25 Under this guiding principle, the CCP aims to balance state-led development with the well-being of its citizens. By advocating for socialism with Chinese characteristics, Xi stresses the importance of prioritizing social welfare, public services, and improving living standards. This approach seeks to ensure that the state’s economic and social policies are aligned with the needs and aspirations of the people, reinforcing the notion that the people are the true masters of the country.
6. “Govern through the Rule of Law.” Socialism with Chinese characteristics26 is safeguarded by laws that require deeper judicial27 reforms28 and the enhancement of national29 moral quality.30 Chairman Xi has emphasized the importance of judicial reform and national morality to ensure a just and orderly society. However, the CCP remains the ultimate31 authority32 in interpreting and enforcing laws. This governance approach aims to balance legal frameworks with the Party’s overarching control, striving to uphold legal standards while maintaining the Party’s central role in the administration of justice and societal governance.
7. “Practice socialist core values, including Marxism, Communism, and Socialism with Chinese characteristics.” Chairman Xi has consistently emphasized that confidence in China’s political culture33 is a profound driving force34 for the nation’s development.35 By promoting the core values of Marxism, Communism, and Socialism with Chinese characteristics, Xi aims to strengthen ideological commitment and national identity. This confidence in political culture serves as a foundation for social unity and resilience, supporting the Party’s vision of a prosperous, stable, and progressive society. Through these values, the CCP seeks to inspire and guide the nation’s development path.
8. “Improving people’s livelihood and well-being is the primary goal of development.” Drawing inspiration from Sun Yat-Sen,36 Xi Jinping emphasizes that public contentment is essential for domestic stability,37 peace, and order. By stressing “common prosperity,” Xi aims to reduce the wealth gap and ensure equitable economic growth.38 This focus on improving livelihoods highlights the Party’s commitment to social welfare, healthcare, education, and employment opportunities. By prioritizing the well-being of all citizens, the CCP seeks to foster a harmonious and stable society, reinforcing the legitimacy of its governance.
9. “Coexist with nature.” Xi Jinping emphasizes the importance of basic national policies for environmental protection39 and energy conservation,40 believing they contribute to global ecological safety and safeguard China’s priceless natural assets. This commitment is reflected in Xi’s efforts41 to position China as a leader42 in green technology.43 By promoting sustainable practices and investing in renewable
energy, the CCP aims to mitigate environmental degradation and support global efforts to combat climate change. This approach underscores China’s responsibility to both its own environment and the broader global ecosystem.
10. “Strengthen national security.” Under Chairman Xi’s administration, major principles for national safety include coordinating development and security, strengthening awareness, and preparing for crises in times of peace.44 This strategic approach is reflected in the PLA’s focus on combat readiness.45 Xi emphasizes the importance of integrating national security into all aspects of governance, ensuring that China is well-prepared to address both internal and external threats. By enhancing military capabilities and fostering a culture of vigilance, the Party aims to safeguard the nation’s sovereignty and maintain stability in an increasingly complex global environment.
11. “The Communist Party maintains absolute authority over the People’s Liberation Army.” Chairman Xi’s reforms have reinforced the Party’s control over the military through comprehensive political education,46 continuous reforms,47 and advancements in science and technology.48 By enhancing legal management49 within the PLA, these reforms ensure that Party authority50 remains unchallenged. The focus on ideological indoctrination and modernization of military capabilities aligns the PLA closely with the Party’s objectives, maintaining its loyalty and readiness to serve the state under the absolute command of the Communist Party.
12. “One Country – Two Systems for Hong Kong and Macau; One-China 1992 Consensus and Eventual Taiwan Reunification.” Xi Jinping maintains the Party’s flexible, patient,51 yet dogged determination52 to assert its governing authority over all of China.53 The “One Country, Two Systems” principle allows Hong Kong and Macau54 to retain distinct administrative and economic systems, while the One-China 1992 Consensus55 underscores the Party’s commitment to eventual reunification with Taiwan.56 Xi’s approach reflects a strategic balance of firmness and adaptability, aiming to ensure national sovereignty and territorial integrity while accommodating regional differences.
13. “The Chinese dream is inseparable from a peaceful international environment and a stable international order.” Chairman Xi has promoted China’s system57 as an alternative58 to Western liberalism,59 advocating for a model that emphasizes state sovereignty, non-interference, and mutual respect. This approach contributes to the concept of a global “shared destiny,”60 wherein countries cooperate to achieve common goals while respecting each other’s unique development paths. Xi’s vision seeks to position China as a leader in fostering international stability and cooperation, aligning with the broader goal of realizing the Chinese dream in a harmonious global context.
14. “Enforce Party Discipline.” Chairman Xi’s anti-corruption campaign61 is the most visible62 sign of his belief in the importance of the Party’s internal supervision, political purity, and close ties with the masses.63 Xi has emphasized that the Communist Party must uphold strict discipline to maintain its legitimacy and effectiveness. By targeting unhealthy tendencies64 and corruption,65 the campaign seeks to strengthen the Party’s internal culture and ensure that its members adhere to high moral and ethical standards. This focus on discipline and integrity is essential for reinforcing public trust and achieving the Party’s long-term goals.
Insights for the Marine Corps
The above Fourteen Commitments provide a valuable framework for scoping and understanding the often expansive and nebulous nature of “Xi Jinping Thought.” They provide insights into enduring priorities for Xi Jinping as he seeks to maintain the CCP’s monopoly on political power at home and avoid the always-possible spectre of a Soviet-style collapse in the future. Themes that come to the fore include the pervasiveness of Communist Party authority in broader Chinese society, the populist need to frame Party activities as “serving the needs of the masses,” and the importance of maintaining “ideological rigor” and “internal unity” within the party and military, the better to secure the loyalty of the latter for the former. “Xi Jinping Thought” likewise provides a template for the type of authoritarian governance model that Beijing would gladly export abroad, the better to nurture a group of like-minded nations to help “make the world safe” for CCP-style authoritarianism. The Marine Corps’ continued operations, activities, and investments in support of a free and open Indo-Pacific can be more effectively calibrated via an understanding, outlined by Xi Jinping Thought, of how Beijing seeks to incrementally undermine that same order in the hearts and minds of its neighbors’ citizens.
>Mr. Jensen is a recognized expert in Sino-Russian relations and information operations. He is the author of the “Shanghai Weekly” and related pacing threat-focused products widely distributed throughout the U.S. and Allied maritime forces. He currently consults as the Senior RED (Russo-Chinese) Subject-Matter Expert for the Marine Corps Vandegrift Team, a coordinating tiger cell under the Marine Corps Deputy Commandant for Information focused on optimizing the broader U.S. maritime force and key partners for Great-Power Competition in the Information Domain.
Notes
1. China Central TV-1, “His Own Words: The 14 Principles of ‘Xi Jinping Thought,’” BBC Monitoring, October 24, 2017, https://monitoring.bbc.co.uk/product/c1dmwn4r.
2. Chris Buckley, “Xi Jinping Thought Explained: A New Ideology for a New Era,” The New York Times, February 26, 2018, https://www.nytimes.com/2018/02/26/world/asia/xi-jinping-thought-explained-a-new-ideology-for-a-new-era.html.
3. Jarek Grzywacz, “How Xi Jinping Used the CCP Constitution to Cement His Power,” The Diplomat, January 26, 2023, https://thediplomat.com/2023/01/how-xi-jinping-used-the-ccp-constitution-to-cement-his-power.
4. Charlotte Poirier, “Xi Jinping Thought: Xi’s Struggle against Political Decline,” Institute for Security and Development Policy, 2021, https://www.isdp.se/publication/xi-jinping-thought-xis-struggle-against-political-decline.
5. Mercy A. Kuo, “The Political Aims of ‘Xi Jinping Thought,’” The Diplomat, November 21, 2023, https://thediplomat.com/2023/11/the-political-aims-of-xi-jinping-thought.
6. Congressional Research Service, “China Primer: China’s Political System–CRS Reports,” Congressional Research Service, January 3, 2025, https://crsreports.congress.gov/product/pdf/IF/IF12505.
7. Timothy R. Heath, “Xi’s Cautious Inching Towards the China Dream,” RAND, August 11, 2023, https://www.rand.org/pubs/external_publications/EP70200.html.
8. Michał Bogusz and Jakub Jakóbowski, “The Chinese Communist Party and Its State. Xi Jinping’s Conservative Turn,” OSW Report, April 2020, https://www.osw.waw.pl/sites/default/files/REPORT_The-Chinese-Communist-Party_net.pdf.
9. William Zheng, “China’s Top Universities Told to Stop Slacking off on Communist Party Ideology,” South China Morning Post, September 7, 2021, https://www.scmp.com/news/china/politics/article/3147779/chinas-top-universities-told-stop-slacking-communist-party.
10. Scott Livingston, “The Chinese Communist Party Targets the Private Sector,” CSIS, October 8, 2020, https://www.csis.org/analysis/chinese-communist-party-targets-private-sector.
11. Nis Grünberg and Katja Drinhausen, “The Party Leads on Everything,” Merics, September 24, 2019, https://merics.org/en/report/party-leads-everything.
12. David Bulman, Cui Wei, Mark Frazier, Mike Mike Gow, Yujeong Yang, Guoguang Wu, and Mary Gallagher, “Xi Jinping Says He Wants to Spread China’s Wealth More Equitably. How Likely Is That to Actually Happen?” ChinaFile, March 3, 2023, https://www.chinafile.com/conversation/common-prosperity-China-wealth-redistribution.
13. Thomas Hale and Leila Abboud, “Xi Jinping’s Call for Wealth Redistribution Threatens Luxury Groups’ China Boom,” Financial Times, August 27, 2021, https://www.ft.com/content/4cf59a34-cd03-48a1-b5d0-0c71922ef9b3.
14. Josephine Ma, “My Take: Why China Needs to Mind the Earnings Gap,” South China Morning Post, January 30, 2024, https://www.scmp.com/news/china/article/3250334/why-china-needs-mind-earnings-gap.
15. Yew Lun Tian, “Unleashing Reforms, Xi Returns to China’s Socialist Roots,” Reuters, September 9, 2021, https://www.reuters.com/world/china/unleashing-reforms-xi-returns-chinas-socialist-roots-2021-09-09.
16. Maya Wang, “China’s Techno-Authoritarianism Has Gone Global,” Human Rights Watch, April 8, 2021, https://www.hrw.org/news/2021/04/08/chinas-techno-authoritarianism-has-gone-global.
17. Laura He, “China’s ‘unprecedented’ Crackdown Stunned Private Enterprise. One Year on, It May Have to Cut Business Some Slack,” CNN, November 3, 2021, https://www.cnn.com/2021/11/02/tech/china-economy-crackdown-private-companies-intl-hnk/index.html.
18. The Associated Press, “China Bans Effeminate Men on TV,” NPR, September 2, 2021, https://www.npr.org/2021/09/02/
1033687586/china-ban-effeminate-men-tv-official-morality.
19. The Economist, “Xi Jinping Is Obsessed with Political Loyalty in the Pla,” The Economist, November 6, 2023, https://www.economist.com/special-report/2023/11/06/xi-jinping-is-obsessed-with-political-loyalty-in-the-pla.
20. Yu Jie, “China’s New Scientists,” Chatham House, July 2023, https://www.chathamhouse.org/2023/07/chinas-new-scientists.
21. Ben Murphy, Rogier Creemers, Elsa Kania, Paul Triolo, Kevin Neville, and Graham Webster, “Xi Jinping: ‘Strive to Become the World’s Primary Center for Science and High Ground for Innovation,’” DigiChina, March 18, 2021, https://digichina.stanford.edu/work/xi-jinping-strive-to-become-the-worlds-primary-center-for-science-and-high-ground-for-innovation.
22. Marina Rudyak, “Cooperation/合作,” Decoding China, March 26, 2023, https://decodingchina.eu/cooperation.
23. William Langley, “Xi Jinping Framed as Man of the People and the Party in New Year’s Speech,” South China Morning Post, January 1, 2021, https://www.scmp.com/news/china/politics/article/3116129/xi-jinping-framed-man-people-and-party-new-years-speech.
24. Joe C.B. Leung, “Common Prosperity: A Conundrum for China,” AsiaGlobal Online Journal, October 21, 2021, https://www.asiaglobalonline.hku.hk/common-prosperity-conundrum-china.
25. Mimi Lau, “Xi Declares Extreme Poverty Has Been Wiped out in China,” South China Morning Post, February 25, 2021, https://www.scmp.
com/news/china/politics/article/3123174/xi-jinping-declares-extreme-poverty-has-been-wiped-out-china.
26. Ethan Paul and Lea Li, “What Is ‘Socialism with Chinese Characteristics’?” South China Morning Post, June 26, 2021, https://www.scmp.com/video/china/3138788/socialism-chinese-characteristics-explained.
27. Political Bureau of the CCP Central Committee, “Xi Jinping Emphasized Strengthening the Development of the Legal System Related to Foreign Affairs and Creating Favorable External Environment and Rule of Law Conditions during the Tenth Collective Study Session of the CCP Central Committee Politburo,” CSIS Interpret: China, November 28, 2023, https://interpret.csis.org/translations/xi-jinping-emphasized-strengthening-the-development-of-the-legal-system-related-to-foreign-affairs-and-creating-favorable-external-environment-and-rule-of-law-conditions-during-the-tenth-collective-st.
28. The Economist, “Why China’s Government Is Hushing up Court Rulings,” The Economist, January 15, 2024, https://www.economist.com/china/2024/01/15/why-chinas-government-is-hushing-up-court-rulings.
29. Michael Schuman, “Xi Jinping Is Fighting a Culture War at Home,” The Atlantic, December 20, 2023, https://www.theatlantic.com/international/archive/2023/12/xi-jinping-china-culture-war/676896.
30. Delia Lin, “Morality Politics under Xi Jinping,” East Asia Forum, August 1, 2019, https://eastasiaforum.org/2019/08/01/morality-politics-under-xi-jinping.
31. Chris Buckley, “‘Drive the Blade in’: Xi Shakes up China’s Law-and-Order Forces,” The New York Times, August 20, 2020, https://www.
nytimes.com/2020/08/20/world/asia/china-xi-jinping-communist-party.html.
32. Thomas Hale and Xueqiao Wang, “China’s Court Database Reform Stokes Fears for Transparency in Legal Sector,” Financial Times, January 7, 2024, https://www.ft.com/content/665a48d5-2ce0-4661-91c9-6dbebe2e4b9b.
33. Zhuoran Li, “The Sixth Plenum and the Rise of Traditional Chinese Culture in Socialist Ideology,” The Diplomat, November 19, 2021, https://thediplomat.com/2021/11/the-sixth-plenum-and-the-rise-of-traditional-chinese-culture-in-socialist-ideology.
34. News Desk, “Xi Jinping Calls on Writers, Artists to Contribute to National Rejuvenation,” The Global Herald, December 14, 2021, https://theglobalherald.com/news/xi-jinping-calls-on-writers-artists-to-contribute-to-national-rejuvenation.
35. Agence France-Presse, “‘Ode to the New Era’: Chinese Communist Party’s Historical Resolution Explained,” France 24, November 17, 2021, https://www.france24.com/en/live-news/
20211117-ode-to-the-new-era-chinese-communist-party-s-historical-resolution-explained.
36. Benjamin Carlson, “Tug of War over China’s Founding Father Sun Yat-Sen,” Yahoo! News, November 9, 2016, https://sg.news.yahoo.com/
tug-war-over-chinas-founding-father-sun-yat-
045718797.html.
37. Ananth Krishnan, “Domestic Considerations Always Come First for China’s Communist Party: Rana Mitter on the CPC at 100,” The Hindu, July 1, 2021, https://www.thehindu.com/news/international/domestic-considerations-always-come-first-for-chinas-communist-party-rana-mitter-on-the-cpc-at-100/article61448303.ece.
38. Mercy A. Kuo, “China’s ‘Common Prosperity’: The Maoism of Xi Jinping–Insights from Ming Xia,” The Diplomat, September 23, 2021, https://thediplomat.com/2021/09/chinas-common-prosperity-the-maoism-of-xi-jinping.
39. AsiaNews, “Xi Jinping Now Wants Economic Growth to Respect the Environment,” AsiaNews, February 11, 2019, https://www.asianews.it/
news-en/Xi-Jinping-now-wants-economic-growth-to-respect-the-environment-46216.html.
40. Helen Adams, “President of China, Xi Jinping, Declares an End to Coal Use,” Sustainability Magazine, September 22, 2021, https://sustainabilitymag.com/renewable-energy/president-china-xi-jinping-declares-end-coal-use.
41. Dominic Chiu, “The East Is Green: China’s Global Leadership in Renewable Energy,” New Perspectives in Foreign Policy 13 (2017), https://csis-website-prod.s3.amazonaws.com/s3fs-public/171011_chiu_china_Solar.pdf?i70f0uep_pGOS3iWhvwUlBNigJMcYJvX.
42. Erin Black, “Why China Is so Far Ahead of the U.S. in Electric Vehicle Production,” CNBC, March 24, 2021, https://www.cnbc.com/2021/03/24/why-china-is-so-far-ahead-of-the-us-when-it-comes-to-ev-production-.html.
43. Gang Chen,“China’s Quest for Global Climate Leadership,” East Asia Forum, June 24, 2021, https://eastasiaforum.org/2021/06/24/chinas-quest-for-global-climate-leadership.
44. Aadil Brar, “‘Prepare to Fight,’ China Tells Citizens. Xi Jinping Has Big Plans for Party and Security,” ThePrint, November 22, 2021, https://theprint.in/opinion/chinascope/prepare-to-fight-china-tells-citizens-xi-jinping-has-big-plans-for-party-and-security/769639.
45. Ananth Krishnan, “China President Xi Jinping Signs Mobilisation Order for PLA Training,” The Hindu, January 4, 2022, https://www.thehindu.com/news/international/china-president-xi-jinping-signs-mobilisation-order-for-pla-training/article38118147.ece; and Catherine Wong, “Xi Tells China’s Military ‘be Prepared to Respond’ in Unstable Times,” South China Morning Post, March 9, 2021, https://www.scmp.com/news/china/military
/article/3124733/xi-jinping-tells-chinas-military-be-prepared-respond-unstable.
46. Derek Solen, “Right Thinking and Self-Criticisms: Military Modernization with Chinese Communist Characteristics,” The Diplomat, September 29, 2021, https://thediplomat.com/2021/09/right-thinking-and-self-criticisms-military-modernization-with-chinese-communist-characteristics.
47. William Zheng, “PLA Targets Top Brass in Loyalty Education Campaign after High-Level Purges,” South China Morning Post, February 8, 2025, https://www.scmp.com/news/china/politics/article/3297783/chinas-pla-targets-top-brass-campaign-touting-political-loyalty-xi-jinping.
48. Elsa B. Kania, “In Military-Civil Fusion, China Is Learning Lessons from the United States and Starting to Innovate,” The Strategy Bridge, August 27, 2019, https://thestrategybridge.org/the-bridge/2019/8/27/in-military-civil-fusion-china-is-learning-lessons-from-the-united-states-and-starting-to-innovate..
49. James Mulvenon, “‘Comrade, Where’s My Military Car?’ Xi Jinping’s Throwback Mass-Line Campaign to Curb PLA Corruption,” China Leadership Monitor, No. 42 (2013), https://www.hoover.org/sites/default/files/uploads/documents/CLM42JM.pdf.
50. Mathieu Duchâtel, ed, “The PLA Reforms: Tightening Control over the Military: Foundation for Strategic Research,” European Council on Foreign Relations, March 31, 2016, https://www.frstrategie.org/en/publications/others/pla-reforms-tightening-control-over-military-2016.
51. Xin Ge, “Why ‘one Country, Two Systems’ Is Successful in Hong Kong and Macao?” Modern Diplomacy, January 14, 2024, https://moderndiplomacy.eu/2024/01/14/why-one-country-two-systems-is-successful-in-hong-kong-and-macao; and Ezra Cheung, Lo Hoi-ying, and Willa Wu, “Hong Kong Governing Principle to Be Permanent Feature, Top Beijing Official Says,” South China Morning Post, February 26, 2024, https://www.scmp.com/news/hong-kong/politics/article/3253216/beijing-attaches-great-importance-hong-kong-countrys-global-finance-hub-xia-baolong-tells-local
52. Dzirhan Mahadzir, “Xi Jinping Pledges Reunification with Taiwan in New Year’s Message,” USNI News, January 1, 2024, https://news.usni.org/2024/01/01/xi-jinping-pledges-reunification-with-taiwan-in-new-years-message; and William Zheng, “Xi Jinping’s Firm Hand on Hong Kong and Taiwan Backed by Communist Party,” South China Morning Post, November 12, 2021, https://www.scmp.com/news/china/politics/article/3155755/chinas-communist-party-backs-xi-jinpings-firm-hand-hong-kong.
53. Colin Clark, “New Chinese 10-Dash Map Sparks Furor across Indo-Pacific: Vietnam, India, Philippines, Malaysia,” Breaking Defense, September 4, 2023, https://breakingdefense.com/2023/09/new-chinese-10-dash-map-sparks-furor-across-indo-pacific-vietnam-india-philippines-malaysia.
54. William H. Overholt, “Hong Kong: The Rise and Fall of ‘One Country, Two Systems,’” Harvard Kennedy School, December 2019, https://ash.harvard.edu/wp-content/uploads/2024/02/overholt_hong_kong_paper_final.pdf; and Sophie Williams, “Macau: China’s Other ‘one Country, Two Systems’ Region,” BBC News, December 19, 2019, https://www.bbc.com/news/world-asia-china-50832919.
55. Alyssa Resar, “The 1992 Consensus: Why It Worked and Why It Fell Apart,” The Diplomat, July 18, 2022, https://thediplomat.com/2022/07/the-1992-consensus-why-it-worked-and-why-it-fell-apart.
56. Helen Davidson, “China and Taiwan Are Destined for ‘Reunification’, Xi Tells Former President,” The Guardian, April 10, 2024, https://www.theguardian.com/world/2024/apr/10/china-taiwan-destined-for-reunification-xi-jinping-tells-ma-ying-jeou.
57. Dylan Levi King, “Wang Huning: The Man behind Xi Jinping,” The Spectator, July 27, 2021, https://www.spectator.co.uk/article/the-man-behind-xi-jinping.
58. Christopher Colley, “The Fallacy of a Chinese Alternative to the Western Order,” Wilson Center, January 18, 2024, https://www.wilsoncenter.org/article/fallacy-chinese-alternative-western-order.
59. Scott Foster, “The Chinese Communist Party vs Western Liberalism,” Asia Times, December 25, 2020, https://asiatimes.com/2020/12/the-chinese-communist-party-vs-western-liberalism.
60. Robert A. Manning, “China’s Developing World Promises Are Smoke and Mirrors,” Foreign Policy, May 8, 2024, https://foreignpolicy.com/2024/04/05/china-developing-world-bri-global-development-initiative-hegemony.
61. William Zheng, “‘No Mercy’ in Anti-Corruption Drive, Xi Warns Communist Party,” South China Morning Post, January 12, 2022, https://www.scmp.com/news/china/politics/article/3163016/xi-jinping-his-top-leadership-no-mercy-fight-against-corruption.
62. Fatoumata Diallo, “Xi Jinping’s Anti-Corruption Struggle: Eight Years On,” Institute for Security and Development Policy, April 9, 2021, https://web.archive.org/web/20211216205930/https://isdp.eu/content/uploads/2021/04/Xi-Jinpings-Anti-corruption-Struggle-IB-09.04.21.pdf.
63. Perry Link, “The CCP’s Culture of Fear,” ChinaFile, October 21, 2021, https://www.chinafile.com/library/nyrb-china-archive/ccps-culture-of-fear. Cheryl Teh, “China Punished More than 600,000 Officials in 2021 amid Xi Jinping’s Clampdown on Corruption and Misconduct,” Business Insider, January 23, 2022, https://www.businessinsider.com/china-punished-over-600000-officials-amid-xis-corruption-clampdown-2022-1. Eva Fu, “Chinese State Media Orders US Workers to Maintain ‘political Purity,’ Not Practice Falun Gong: Internal Document,” The Epoch Times, December 2, 2021, https://www.theepochtimes.com/china/chinese-state-media-orders-us-workers-to-maintain-political-purity-not-practice-falun-gong-internal-document-4135242; and James Griffiths, “Analysis: Xi Jinping’s Culture War Comes to China’s Campuses as Communist Party Prepares to Mark 100 Years,” CNN, April 20, 2021, https://www.cnn.com/2021/04/20/china/xi-jinping-universities-intl-hnk/index.html; and Katsuji Nakazawa, “Analysis: XI Aims to Mobilize the Masses with Populist Crackdowns,” Nikkei Asia, August 12, 2021, https://asia.nikkei.com/Editor-s-Picks/China-up-close/Analysis-Xi-aims-to-mobilize-the-masses-with-populist-crackdowns.
64. Reuters, “China Culture Crackdown a Sign of ‘profound’ Political Change,” Reuters, August 31, 2021, https://www.reuters.com/world/china/china-culture-crackdown-sign-profound-political-change-commentary-2021-08-31.
65. Jacob Fromer, “Xi’s Iron Grip on Power Brings New Form of Corruption, US Panel Is Told,” South China Morning Post, January 28, 2022, https://www.scmp.com/news/china/article/3165022/xi-jinpings-iron-grip-power-brings-new-form-corruption-china-experts.